Graphiant provides the user with a unique solution by simplifying enterprise connectivity. Our solution allows the user to monitor traffic usage within our unified network, collect data, and apply business logic to influence packet and circuit paths.
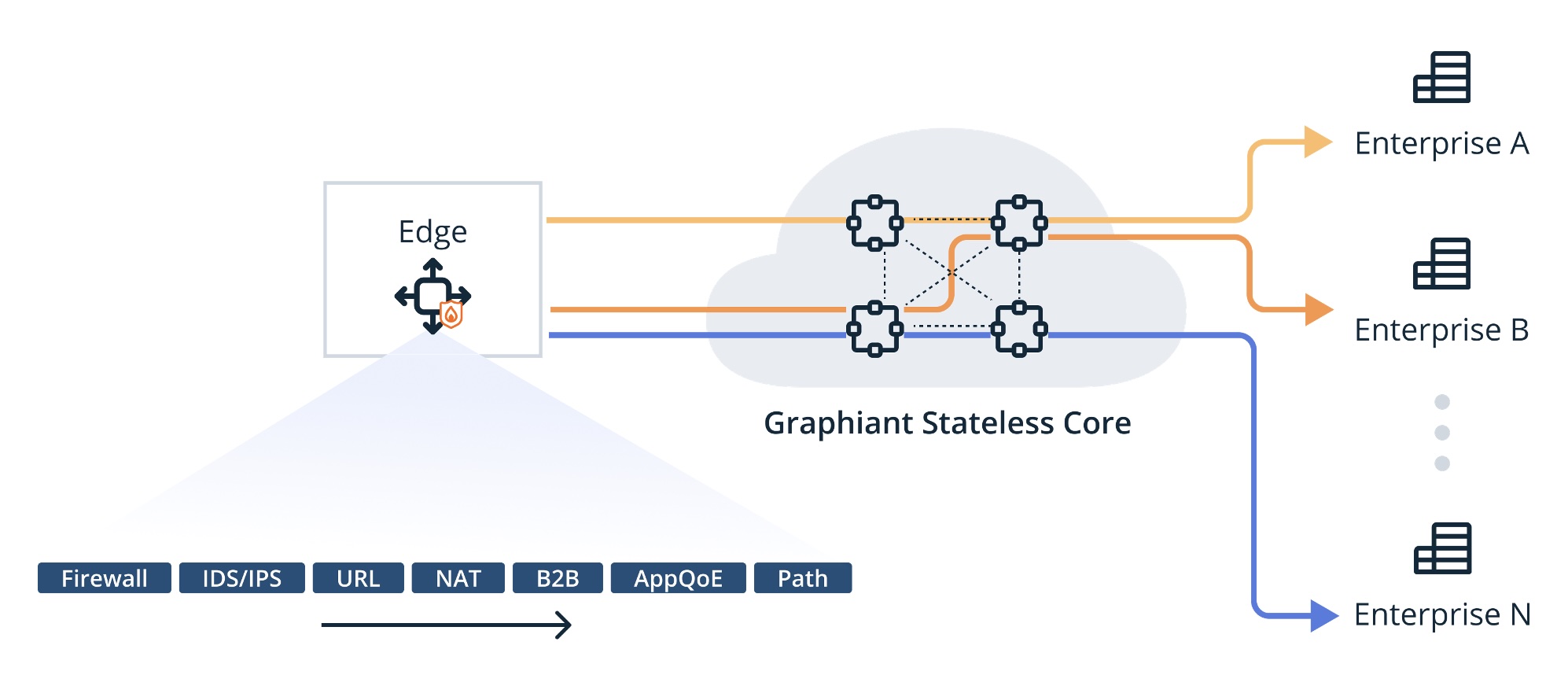
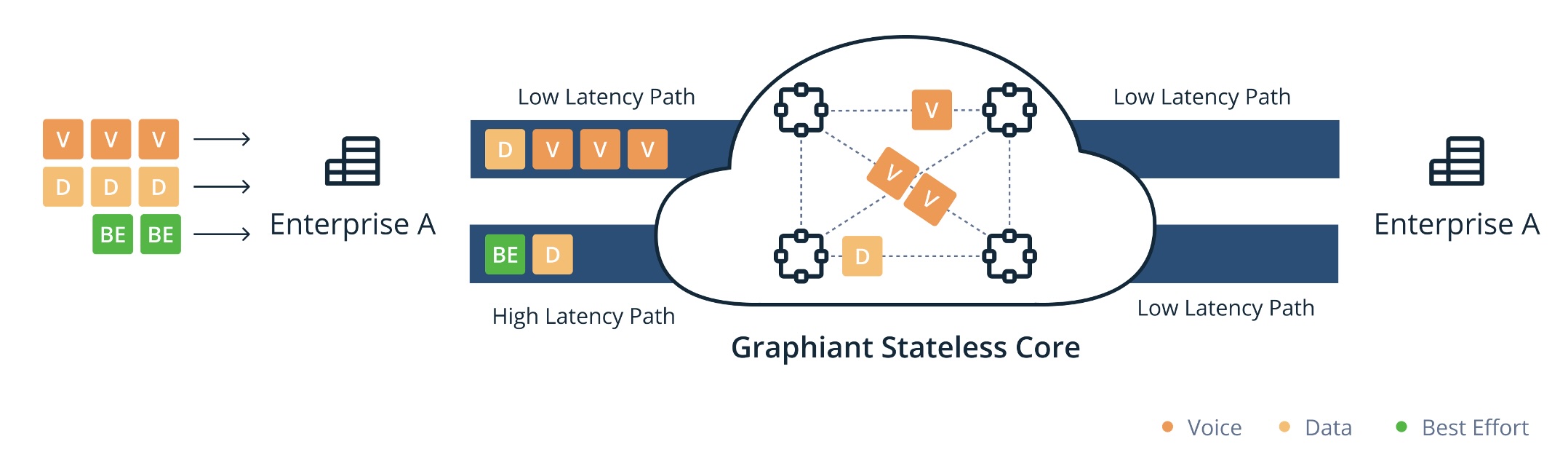
We have two filter-based classifications, Data Plane and Control Plane requirements.
Data Plane attributes for implementing data plane policies including Security, SLA based routing, QoS, etc.
Control Plane attributes for implementing control policies for ODP, BGP and OSPF.
Data Plane Requirements include:
Zone-based Classification - Zones can defined around a minimum instance being an interface, meaning that multiple zones can exist in a VRF
Local/Host Zone for local node - Traffic destined to the node itself
Policy Support for DPI APP-ID matching - Security policies should allow for matching of L3, L4 and L7 addresses, ports and signatures respectively (See deep packet inspection article)
Country Specific Blocking Capability - Have the ability to define simple policy rules that block traffic from/to specific countries in the world
IP Fragments - Ability to match on IP fragments
IP Broadcast/Subnet Broadcast - Match packets addressed to a subnet broadcast address
IP Options blocking - Match packets with IP options
IPv6: Block Source Routing EH - Match on packets containing IPv6 Source routing header
IPv6: Generic EH blocking - Match on packets with specified extensions header(s)
URL Matching - Identify URLs by subdomain.domain and match REGEX for HTTP. For HTTPs (TLS1.2) match on Certificate X.509 Common Name
Application specific classification - Identify TCP, Fragments from other packets of the flow
User defined application classification - User should be able to define application based on IP header
VPN as a source/destination - Traffic originated or destined to a given VPN
Traffic traversing the Overlay - Traffic destined to or received from overlay
Traffic sent to underlay (DIA) - Traffic not routed on the overlay but rather on the underlay
Traffic Identification based on egress GW service/Edge site group
Traffic stays within the site (LAN2LAN) - Intra-Site Traffic classification
Source/Destination Interface - WAN or WAN circuit name/id
Control Plane ODP Requirements include:
Prefix List - able to match IP routing prefix
Site ID/Site List - Match on the site-id where the prefix was originated
Circuit ID - Route-NHOP attribute
VPN Identifier - Match on routes within a VPN
AS-Path - Match on AS-Path
Route Tag - Match on Tags associated with routes
Community - Match on community
EID, Route-Distinguisher, Route Target - Match on Enterprise and VRF identifiers
Control Plane OSPF Requirements include:
Prefix List - IP prefix list
Route-Type - Match on Inter-area, Intra-area and External
Route-Tag - Match on route tags
Control Plane BGP Requirements include:
Prefix List - Match on IP prefixes
AS-Path - Match on AS-Path
Communities - Match on standard and extended communities
Route-Tag - Match on route-tag